- Topic1/3
15k Popularity
34k Popularity
18k Popularity
6k Popularity
172k Popularity
- Pin
- Hey fam—did you join yesterday’s [Show Your Alpha Points] event? Still not sure how to post your screenshot? No worries, here’s a super easy guide to help you win your share of the $200 mystery box prize!
📸 posting guide:
1️⃣ Open app and tap your [Avatar] on the homepage
2️⃣ Go to [Alpha Points] in the sidebar
3️⃣ You’ll see your latest points and airdrop status on this page!
👇 Step-by-step images attached—save it for later so you can post anytime!
🎁 Post your screenshot now with #ShowMyAlphaPoints# for a chance to win a share of $200 in prizes!
⚡ Airdrop reminder: Gate Alpha ES airdrop is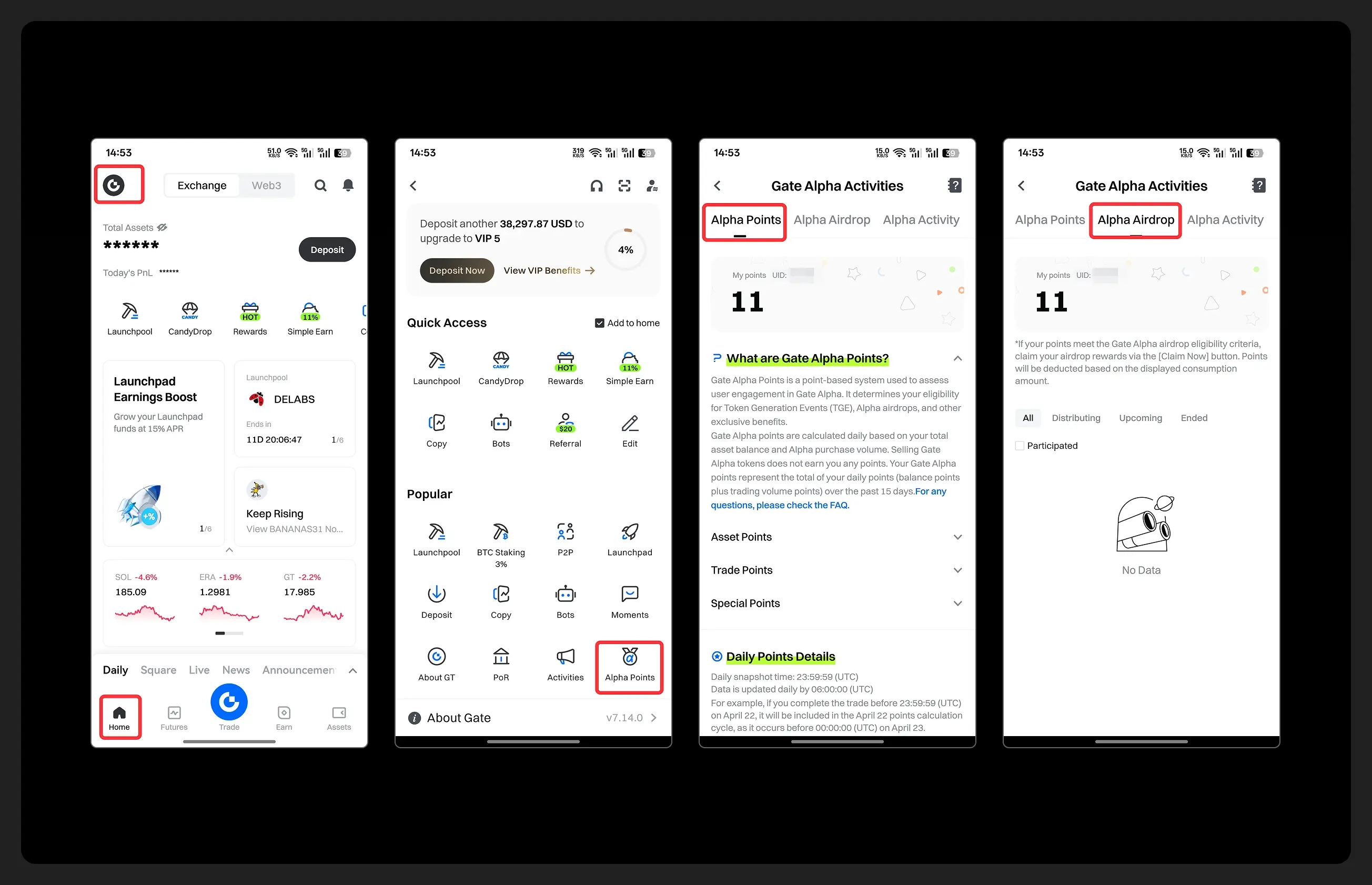
- Gate Futures Trading Incentive Program is Live! Zero Barries to Share 50,000 ERA
Start trading and earn rewards — the more you trade, the more you earn!
New users enjoy a 20% bonus!
Join now:https://www.gate.com/campaigns/1692?pid=X&ch=NGhnNGTf
Event details: https://www.gate.com/announcements/article/46429
- Hey Square fam! How many Alpha points have you racked up lately?
Did you get your airdrop? We’ve also got extra perks for you on Gate Square!
🎁 Show off your Alpha points gains, and you’ll get a shot at a $200U Mystery Box reward!
🥇 1 user with the highest points screenshot → $100U Mystery Box
✨ Top 5 sharers with quality posts → $20U Mystery Box each
📍【How to Join】
1️⃣ Make a post with the hashtag #ShowMyAlphaPoints#
2️⃣ Share a screenshot of your Alpha points, plus a one-liner: “I earned ____ with Gate Alpha. So worth it!”
👉 Bonus: Share your tips for earning points, redemption experienc
- 🎉 The #CandyDrop Futures Challenge is live — join now to share a 6 BTC prize pool!
📢 Post your futures trading experience on Gate Square with the event hashtag — $25 × 20 rewards are waiting!
🎁 $500 in futures trial vouchers up for grabs — 20 standout posts will win!
📅 Event Period: August 1, 2025, 15:00 – August 15, 2025, 19:00 (UTC+8)
👉 Event Link: https://www.gate.com/candy-drop/detail/BTC-98
Dare to trade. Dare to win.
Ten steps to build a strong encryption asset protection system.
Top Ten Steps to Ensure Asset Security
In today's complex cryptocurrency environment, protecting your digital assets is crucial. This article will introduce ten simple yet effective steps to help you enhance your ability to guard against phishing and other fraudulent activities, ensuring your encryption journey is safe and smooth.
1. Establish a Digital Vault
For long-term holding of encryption, creating a multi-signature wallet is a wise choice. This type of wallet is often referred to as a "vault," requiring multiple private keys to authorize any transaction, significantly enhancing asset security. Even if one of the private keys is leaked, your assets remain secure.
It is recommended to start with a 2-of-3 multi-signature strategy and consider using a hardware wallet as one of the signers to further enhance the level of security.
2. Establish a Risk Wallet
Daily activities such as airdrop claims or NFT minting should use a dedicated risk wallet, rather than your main vault. Only top up this wallet with a small amount of cryptocurrency when necessary.
Some services allow you to delegate the permissions of your vault wallet to a risk wallet without actually moving or jeopardizing any assets. This way, even if the risk wallet inadvertently signs a malicious transaction, your long-term savings will not be affected.
3. Using the Transaction Preview Tool
Download the trading preview tools that help you visualize trading information before you approve anything. These free browser extensions will pop up windows explaining all suggested trades, serving as an important barrier against phishing.
4. Review Token Expenditure Permissions
Regularly check and revoke or minimize unlimited token spending approvals. Many Ethereum-based applications will request "unlimited" token spending approvals, but this can be exploited by attackers. Using specialized platforms makes it easy to modify your token quotas.
5. In-depth Research on the Project
Before using any new project, it is essential to conduct thorough research. Review the project's documentation, FAQs, whitepapers, etc., to understand its details and risk status. If you cannot find quality documentation and educational resources, that in itself is a warning sign.
6. Monitor Asset Status
Use a portfolio tracker to closely monitor your encryption currency positions. These tools provide an overview of assets across various wallets and platforms, allowing you to monitor the situation in real-time. Regular checks not only help observe profits but also timely identify potential asset security vulnerabilities.
7. Stay Updated on Industry Trends
Stay updated on cryptocurrency news, especially recent security incidents. Being informed in a timely manner can help you take action before potential impacts occur. Follow reliable news sources and social media accounts that can quickly provide analysis and interpretation of important events.
8. Strengthen Web2 security measures
Even outside of Web3, it is important to pay attention to protecting personal information. Implement strong operational security measures, including:
9. Develop Emergency Strategies
Prepare for the worst-case scenario. Consider using Web3 security services that can create custom backup wallets and emergency button systems. These tools allow you to quickly transfer assets to a pre-designated secure wallet when you feel a security threat.
Advanced users can explore more complex monitoring and protection services to detect and mitigate on-chain attacks at the millisecond level.
10. Report Suspicious Activities Promptly
If you encounter phishing or other suspicious activities, please sound the alarm quickly. You can post on social media, share information in relevant groups, or report to dedicated databases. This simple act could help others avoid falling into the same trap.
By following these steps, you can significantly enhance your encryption asset security. Remember, in the fast-evolving world of encryption, staying vigilant and continuously learning is key to ensuring asset security.